Plano only steps
4. Adapt the OpenId settings in tisconfig\deploymentconfigs\<MyDeploymentConfig>\config\config.ini
Setting | Description | Sample |
|---|---|---|
OpenIDClientID | Client Identification - obtainable from the API Console Credentials page | tis |
OpenIDClientSecret | Secret identifier a.k.a password | *** |
OpenIDTokenEndpoint | Token source endpoint | https://!!!identityserver/IdentityService/connect/token |
OpenIDAuthEndpoint | Authorization endpoint | https://!!!identityserver/IdentityService/connect/authorize |
OpenIDRedirectUri | The HTTP endpoint on your server that will receive the response | /tisapi/v1.0/sessions/logonopenidpkce |
OpenIDScopes | Scopes are used by an application during authentication to authorize access to a user's details (see Installation TIS Operatoren.pdf) | openid planosession rolenames spxsession |
OpenIDJWKUri | Metadata entry expressed as a URI for the OpenID Connect Identity Provider (IDP)'s JWK Set or OAuth Client | https://!!!identityserver/IdentityService/.well-known/openid-configuration/jwks |
OpenIDIssuer | OpenID Provider (Issuer) metadata | https://!!!identityserver/identityservice |
OpenIDEndSessionEndpoint | End session endpoint for logoff with OpenID | https://!!!identityserver/IdentityService/connect/endsession |
OpenIDUserInfoEndpoint | User info endpoint | https://!!!identityserver/IdentityService/connect/userinfo |
OpenIDEnableDebugDetails | Enables or disables debug details logging | 0 or 1 |
OpenIDIdentityServer | Name of the openid identity server | !!!identityserver |
OpenIDHeaderMappings | A mapping for better debugging | PlanoSource:TIS |
TISBoardLogOnSite | TIS Board Site URL for Logon | /TISBoard/portal/portal/index.html?openid_finished=true |
TISEditorLogOnSite | TIS Editor URL for Logon | /TISEditor/#!/home |
5. Adapt Plano config
5.1. \plano\Websites\identityservice\appsettings.json
Setting | Description | Sample |
|---|---|---|
clientId | OpenID Client ID | tis |
clientName | OpenID Client Name | TIS |
clientSecrets value | Secret password server hash | *** |
allowedGrantTypes | Allowed grant types | ["authorization_code", "password"] |
identityTokenLifetime | Validity of the identity token in seconds | 60 |
accessTokenLifetime | Validity of the access token in seconds | 300 |
allowedScopes | Allowed scopes of sessions | ["openid", "offline_access", "planosession", "role", "featurepermissions", "IdentityServerApi", "essession", "spxemployeedata", "spxsession", "rolenames"] |
allowOfflineAccess | Switch for allowed offline access | true |
requireConsent | Switch for consent requirement | false |
accessTokenType | Type of the access token | jwt |
requirePkce | Switch for Pkce requirement | true |
requireClientSecret | Switch for ClientSecret requirement | true |
alwaysIncludeUserClaimsInIdToken | Switch for including user Claims in the ID token | true |
redirectUris | Redirect URIs for identity service - all lines needed | "https://mycomputer.mycompany/1/", |
postLogoutRedirectUris | Post logout Redirect URIs | "https://mycomputer.mycompany/1/", |
Partial content of appsetting.json of plano IdentityServer:
{ "clientId": "tis", "clientName": "TIS", "clientSecrets": [{ "value": "***" } ], "allowedGrantTypes": ["authorization_code", "password"], "identityTokenLifetime": 60, "accessTokenLifetime": 300, "allowedScopes": ["openid", "offline_access", "planosession", "role", "featurepermissions", "IdentityServerApi", "essession", "spxemployeedata", "spxsession", "rolenames"], "allowOfflineAccess": true, "requireConsent": false, "accessTokenType": "jwt", "requirePkce": true, "requireClientSecret": true, "alwaysIncludeUserClaimsInIdToken": true, "redirectUris": [ "https://hostname/1/", "https://hostname/1/", "https://hostname/1/tisapi/v1.0/sessions/logonopenidpkce", "https://hostname/1/TISBoard/portal/portal/index.html", ], "postLogoutRedirectUris": [ "https://hostname/1/", ] }5.2. Plano Roster
Check the following configuration keys in plano Roster web.config and adapt the hostname and site name if needed. In our example, host name is mycomputer.mycompany.com and the site name is 1.
<add key="plano.Forecast.TisBoard.Url" value=https://hostname/sitename/TISBoard/portal/portal/index.html /> <add key="plano.TisMode" value="New" />5.3. Set up a TISAdmin user in plano roster
Step | Description | Screenshot |
|---|---|---|
5.3.1 |
|
|
5.3.2 |
| 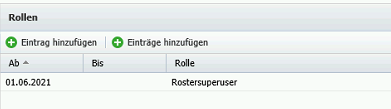 |
5.3.3 |
| 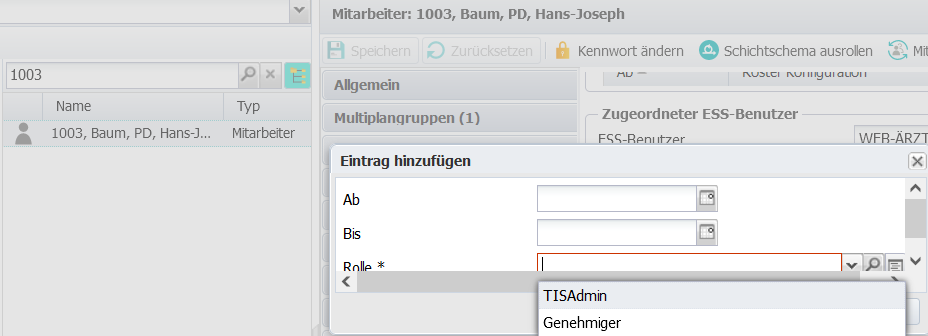 |
5.3.4 |
| 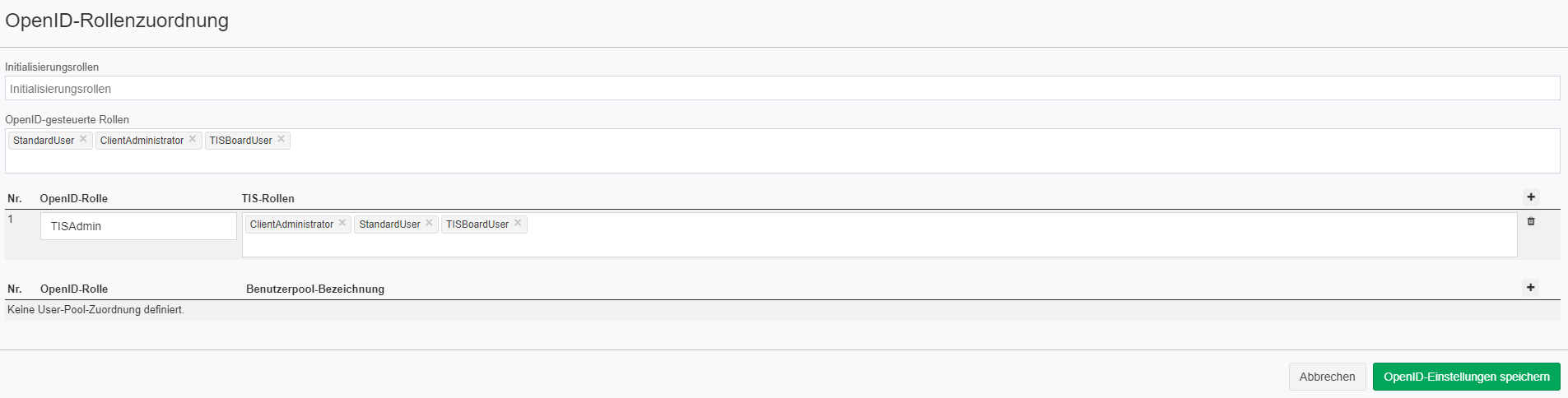 |